


旋转设备


Telink Staff
December 7, 2023
Technology

IoT cybersecurity threats are booming — stay prepared with a proactive security approach to product development.
The Internet of Things (IoT) has revolutionized how we live and work, with billions of devices seamlessly communicating and exchanging data. While IoT offers unprecedented convenience and efficiency, it also presents a growing security risk. According to the 2020 Unit 42 IoT Threat Report, 98% of all IoT devices communicate through messages that are unencrypted, meaning they can easily be circumvented by prying eyes. Another study by Veridify Security found that early 2022 experienced a 77% increase in IoT-targeted malware attacks. With more companies and households integrating smart devices into their everyday environment, cybersecurity in IoT is a necessity.
Consider a smart home — how, at its core, it functions as a network of interconnected devices, each with its unique purpose. Thermostats are remotely set to the perfect indoor temperature, smart light bulbs dim during evening hours, and even fridges maintain ideal temperatures to keep food fresh. But beneath this veneer of convenience lies a potential web of vulnerabilities, including both digital threats like malware and data breaches, and tangible ones like physical attacks.
Weak or default passwords, for instance, can be an open invitation to malicious actors. Another issue arises from the absence of robust encryption as insecure device firmware can crumble under the weight of IoT cybersecurity attacks. Additionally, devices and applications that fail to update in a timely manner risk remaining unguarded as they miss out on crucial bug fixes and security gaps.
In light of these vulnerabilities, regulatory measures have been introduced to establish a standardized framework for technology developers to adhere to, including but not limited to:
Another noteworthy (and recent) regulation in the realm of IoT security is the US Cybersecurity Label, a federal initiative aimed at standardizing security certification for IoT devices. To bring this certification to fruition, the Connectivity Standards Alliance’s (CSA) Product Security Working Group is developing a robust certification program to help IoT developers comply with this new regulation and give consumers better peace of mind with the products they purchase.
As technology continues to evolve, initiatives and regulations like the ones mentioned play an indispensable role in strengthening our digital infrastructure and ensuring that the benefits of IoT innovation are enjoyed without compromising security.
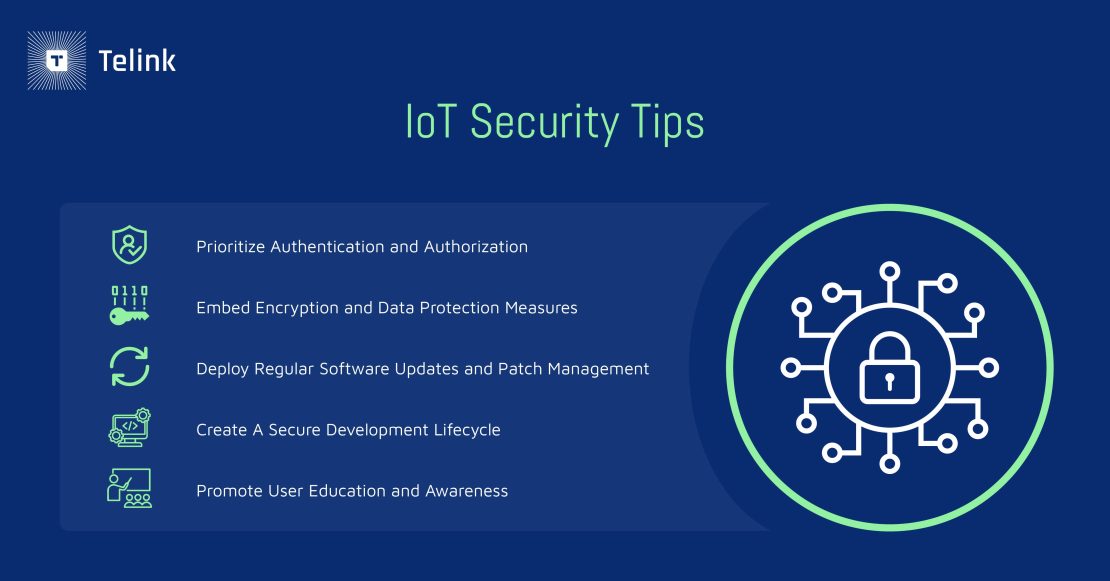
While these regulations may appear to make product and software development more restrictive at first glance, they actually open more opportunities for device capabilities and build long-term consumer trust. As a result, developers should consider implementing the following best practices to enhance the security and quality of their product or solution:
Robust authentication mechanisms form the bedrock of IoT security. Ensuring that users, devices, and servers are precisely who they claim to be is paramount. Implementing multi-factor authentication (MFA) introduces an additional layer of security, making unauthorized access significantly more challenging. Role-based access control also aids in restricting access based on predefined user roles and permissions, which effectively reduces the attack surface and mitigates the potential for unauthorized entry into IoT networks.
Data should be encrypted both at rest and in transit to prevent unauthorized access. Strong encryption algorithms and key management practices are essential for safeguarding sensitive information and protecting it from unauthorized individuals. For example, secure communication protocols like TLS (Transport Layer Security) should be used to exchange data between IoT devices and servers, ensuring data remains confidential at all times.
Maintaining the security of IoT devices requires a proactive stance on software updates and patch management. Regularly releasing and applying firmware updates helps address emerging security vulnerabilities and enhance device security before it’s too late. Encouraging end-users to keep their IoT devices updated with the latest patches is also strongly recommended. To stay ahead of potential threats, continuously monitor for security vulnerabilities and have a robust patch management strategy in place to deploy security patches as soon as they’re needed.
Security should be integrated into the entire product development lifecycle. To identify and address security issues early on, security assessments, code reviews, and penetration testing should be conducted during the development process. Threat modeling is a proactive approach that helps identify potential attack vectors and vulnerabilities, enabling developers to prioritize security measures accordingly. Additionally, providing security training and awareness programs for all stakeholders involved in IoT product development allows for a culture of security consciousness that keeps safety first.
Equipping IoT device users with knowledge of security best practices is a fundamental (and sometimes overlooked) layer of defense. Clear and concise instructions should be provided to guide users on actions such as changing default passwords, enabling security features, and keeping IoT cybersecurity software up to date. Establishing a transparent process for users to report security incidents or any suspicious activity also fosters an environment of trust and vigilance within the IoT ecosystem.
As our smart homes and offices become more integrated, more interoperable, and more intertwined, our lives become easier — but they also become more susceptible to malicious IoT cybersecurity attacks. Therefore, as we move forward in IoT innovation, developers need to stay several steps ahead of those wanting to leverage new technologies for ill intent.
Top-of-the-line security doesn’t have to be complicated. Telink delivers solutions that seamlessly align with the latest IoT standards, elevating security to new heights while expanding creative potential. For example, our multi-protocol SoCs are designed with features like true random number generation, secure boot, root of trust (RoT), hardware encryption accelerator, and more to keep your product safe.
Plus, our SoCs are compatible with the latest IoT standards that go through rigorous certification and testing for a secure foundation that developers and consumers can trust. We also proactively support the IoT product security certification program to be launched by CSA in the near future. By following best practices and partnering with companies like Telink, developers can create IoT ecosystems that are not only innovative but also safe and secure for users. Securing the IoT landscape is a collective effort — partner with Telink to stay ahead of the curve and create safer products for the threats of the future.
Visit our wiki to learn more about our development tools, or ask us a question through our Technical Forum or by contacting us directly today.